Chapter 8
‘Cybersecurity and Risk Management '
"In today’s interconnected world, cybersecurity and risk management are not just IT issues—they are business issues. Protecting supply chains is about protecting the lifeblood of global trade." — Ginni Rometty, former CEO of IBM.
Chapter 7 focuses on the growing importance of cybersecurity and risk management in the digital supply chain. It explores how businesses can mitigate cybersecurity risks by implementing advanced protection measures, including blockchain and cryptographic solutions for securing supply chain data. The chapter also delves into the use of predictive risk analysis to identify and manage potential disruptions before they escalate, as well as the critical role of business continuity planning in ensuring operational resilience amidst global uncertainty. The goal is to equip supply chain leaders with the tools and strategies needed to safeguard operations in an increasingly digital and interconnected environment.
8.1. Mitigating Cybersecurity Risks
As supply chains move toward increased digitalization, they become more interconnected and dependent on technologies such as IoT devices, cloud services, and real-time data analytics. While these advancements offer significant gains in visibility and efficiency, they also introduce critical cybersecurity challenges (Alladi, Ayantoye, and Maple, 2021). A single vulnerability—whether an unsecured sensor or a misconfigured cloud database—can compromise entire networks, posing threats not only to the targeted organization but also to partners, suppliers, and end customers (KPMG, 2022). Consequently, cybersecurity in digital supply chains demands proactive strategies that integrate technical safeguards, policy measures, and cross-industry collaboration.
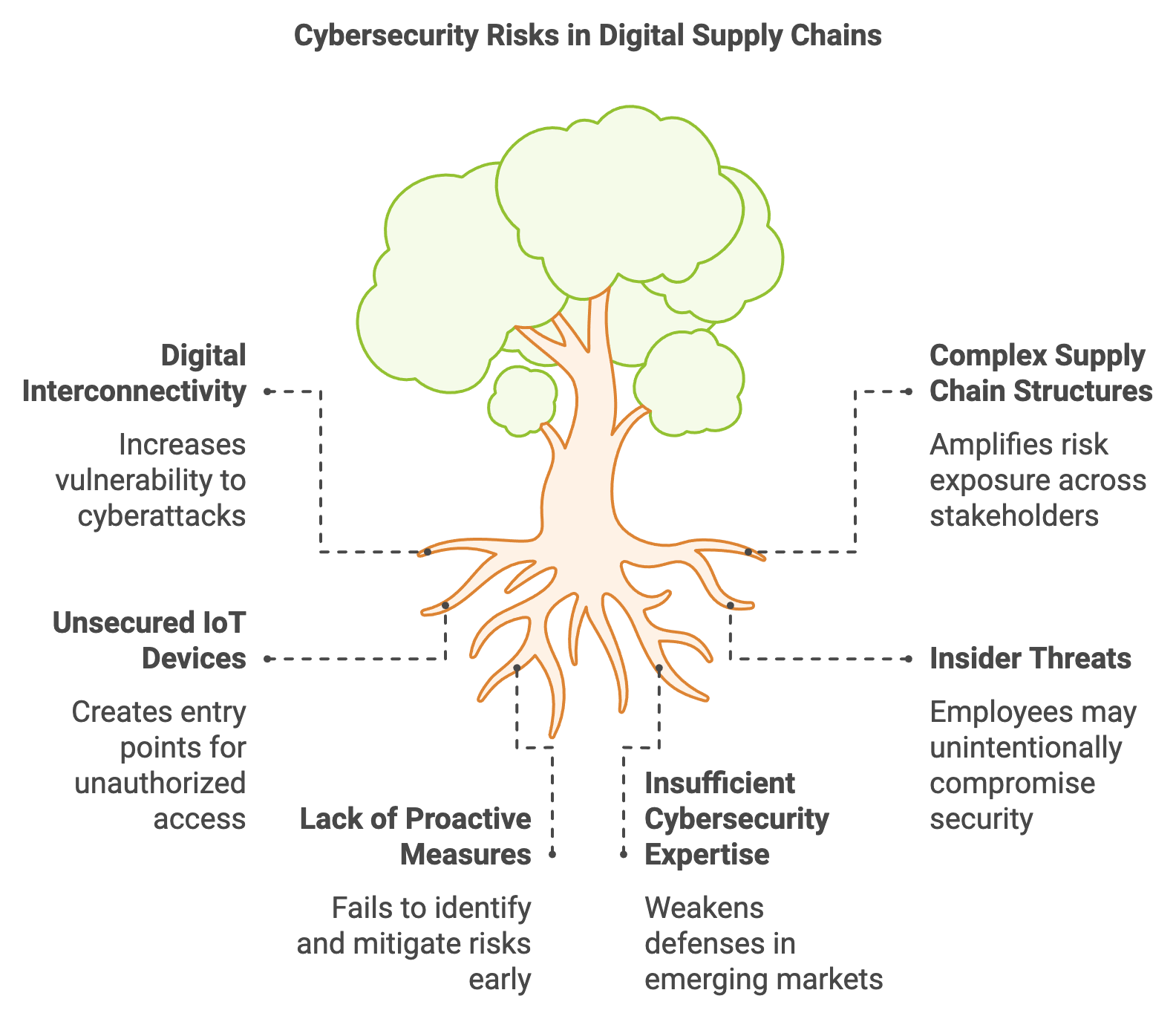
Figure 1: Cybersecurity risks in implementation of digital supply chains.
Among the most pressing risks are data breaches, ransomware attacks, and insider threats. Data breaches can expose confidential information such as pricing data, customer records, or intellectual property, resulting in financial losses and reputational damage (Shen et al., 2022). Ransomware attacks, where adversaries encrypt critical data and demand payment, are particularly devastating for supply chains that rely on uninterrupted operations (Deloitte, 2023). Meanwhile, insider threats—ranging from malicious actions to accidental misuse—highlight the importance of robust access controls and ongoing employee training (PwC, 2024). Given the global, multi-tiered structure of modern supply chains, a successful cyberattack in one node can quickly cascade, disrupting logistics, eroding consumer trust, and triggering regulatory scrutiny.
Academically, the complexity of supply chain cybersecurity spans computer science, risk assessment, and supply chain management (Alladi, Ayantoye, and Maple, 2021). Research consistently shows that organizations best prepared to fend off attacks employ a layered defense approach—combining encryption, continuous monitoring, and identity management with well-developed incident response strategies (Zhang and Li, 2023). For emerging economies, implementing these measures is doubly crucial: it secures nascent digital infrastructure from sophisticated cyber threats and helps local companies integrate securely into global trade networks (EY, 2025).
The 2017 NotPetya malware attack on Maersk exemplifies how rapidly cyber threats can propagate across a global supply chain (KPMG, 2022). The ransomware crippled the shipping giant’s operations, shutting down port terminals, halting deliveries, and causing estimated losses of around $300 million. This incident underscores the importance of hardened network configurations, routine system backups, and real-time threat intelligence. Maersk’s post-attack strategy, which included segmentation of IT networks and heightened incident response capacities, illustrated a robust recovery blueprint. Their experience aligns with broader industry insights that champion proactive, multi-layered defenses over ad hoc, reactive measures (Deloitte, 2023).
Organizations worldwide are increasingly adopting a range of security protocols and frameworks to combat escalating threats:
Security Audits and Vulnerability Assessments: Regular evaluations help detect software weaknesses, misconfigured devices, or outdated patches (PwC, 2024). These audits also ensure compliance with regulations like GDPR or CCPA, minimizing legal risks associated with data breaches.
Zero-Trust Architectures: By treating every access request as potentially malicious, zero-trust models thwart lateral movement by attackers who manage to compromise one part of the system (Zhang and Li, 2023). This approach requires continuous verification of users and devices, limiting unauthorized escalations.
Multi-Factor Authentication (MFA): MFA adds another layer of security beyond mere passwords, making unauthorized access far more difficult. Implementing MFA across all critical systems is a cost-effective means of bolstering defenses (Alladi, Ayantoye, and Maple, 2021).
Collaborative Cybersecurity Partnerships: Many organizations, particularly in emerging markets, partner with specialized cybersecurity firms or consortia to access advanced threat intelligence and skill sets not readily available in-house (EY, 2025). These alliances can provide timely alerts on global threat actors and accelerate coordinated responses.
Emerging technologies offer potent tools for enhancing cybersecurity resilience:
AI-Driven Threat Detection: Machine learning models examine traffic patterns, user behaviors, and system logs for anomalies that may signal an intrusion (Shen et al., 2022). Rapid detection allows for faster, more precise responses, minimizing potential damage or downtime. Over time, these algorithms also adapt to new types of attacks, continually refining their threat profiles (Deloitte, 2023).
IoT Security Frameworks: As IoT devices proliferate, standardized frameworks for device authentication, data encryption, and secure firmware updates become essential. Properly implemented IoT security not only safeguards sensor data but also prevents adversaries from hijacking critical operational technology (KPMG, 2022).
Blockchain for Traceability and Integrity: By logging supply chain transactions on an immutable ledger, blockchain can help verify the authenticity of goods, detect tampering, and ensure transparency across multiple tiers of suppliers (PwC, 2024). Particularly relevant in sectors like pharmaceuticals or luxury goods, blockchain-based approaches minimize counterfeiting and unauthorized modifications.
In developing regions, digital supply chain adoption is often accompanied by limited cybersecurity infrastructure, making them susceptible to state-sponsored actors and criminal networks (EY, 2025). However, integrating best practices from the outset—such as adopting zero-trust models and leveraging cloud-based AI tools—can position these economies to leapfrog vulnerabilities that more established markets confronted during earlier stages of digital transformation. Moreover, building local cybersecurity talent through education and industry alliances fosters sustainable economic development while mitigating the risk of crippling cyberattacks (Zhang and Li, 2023).
Mitigating cybersecurity risks in digital supply chains demands a holistic approach combining technology, policy, and collaborative expertise. Organizations must adopt foundational best practices—regular audits, zero-trust architectures, MFA—and strengthen these measures with emerging innovations like AI-driven threat detection, IoT security frameworks, and blockchain-based traceability (Alladi, Ayantoye, and Maple, 2021). As illustrated by incidents like Maersk’s NotPetya ordeal, failure to invest in robust defenses can lead to extensive financial, operational, and reputational harm (KPMG, 2022). Conversely, a vigilant cybersecurity posture not only protects critical supply chain operations but also fosters trust among partners and customers, ultimately enabling more resilient and innovative global networks (Deloitte, 2023).
8.2. Blockchain and Cryptography for Data Security
Blockchain technology has emerged as a transformative force in securing supply chain operations, offering a decentralized, tamper-proof ledger that assures transparency, traceability, and data integrity (Korpela, Hallikas, and Dahlberg, 2020). Unlike traditional databases that rely on a central authority, blockchain is maintained by a network of participants who validate and record transactions collaboratively. This distributed structure not only eliminates single points of failure but also provides an immutable audit trail, making data manipulation or fraud significantly more challenging. In supply chains, blockchain can track the movement of goods and verify product authenticity, ensuring that every stakeholder—from manufacturers to end consumers—has access to accurate, real-time information (KPMG, 2022). Such capabilities are particularly valuable for global, multi-tiered supply chains often plagued by counterfeiting, mislabeling, and unreliable documentation.
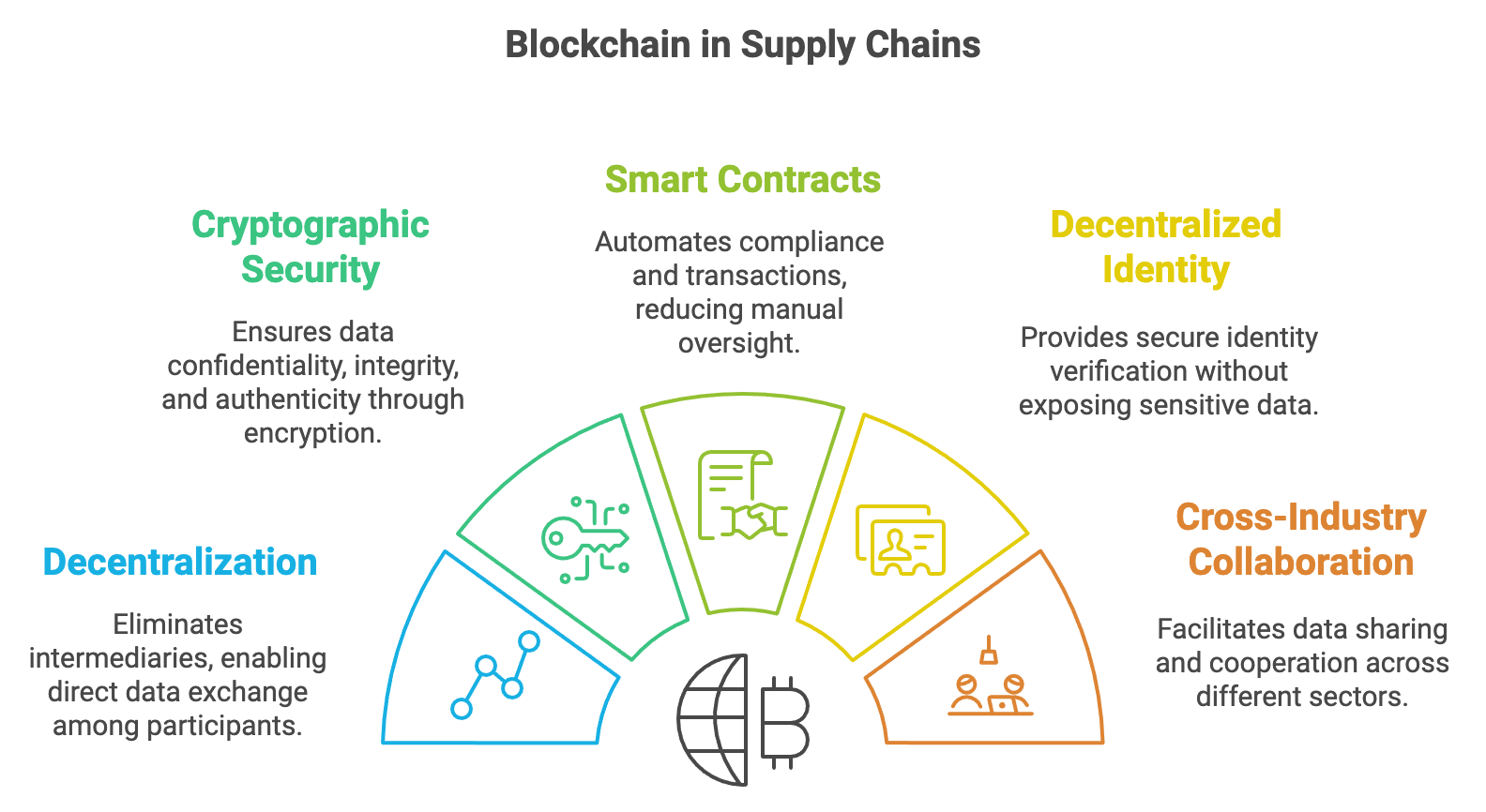
Figure 2: Potential benefits of Blockchain in Supply Chains.
Blockchain’s reliability stems largely from robust cryptographic methods that protect the confidentiality and integrity of data (Gupta, Gupta, and Kumari, 2022). Hashing is a key mechanism, transforming input data into a fixed-length hash value. Even minute alterations in the original data yield entirely different hashes, making tampering instantly detectable. Digital signatures further tighten security by requiring each user to sign transactions with a private key, verifiable by a corresponding public key—ensuring the authenticity of information and preventing unauthorized access (Deloitte, 2023). Additionally, encryption safeguards sensitive data, rendering it unreadable except by authorized entities holding the requisite decryption keys. Together, these cryptographic techniques fortify blockchain-based supply chains against unauthorized modifications, data breaches, and potential privacy infringements (PwC, 2024).
From an academic viewpoint, implementing blockchain in supply chains cuts across fields like distributed systems, cryptography, and operations management. Researchers consistently spotlight its potential to increase trust, reduce fraud, and enhance efficiency, while also highlighting obstacles such as network scalability, legal frameworks, and cost (Korpela, Hallikas, and Dahlberg, 2020). For emerging markets, the allure of a secure, decentralized ledger is particularly pronounced: it can bolster local industries’ integration into global trade networks, providing reliable quality assurance and traceability despite limited infrastructure (EY, 2025).
Pharmaceuticals have been early adopters of blockchain to mitigate risks associated with counterfeit medications and product recalls (Gupta, Gupta, and Kumari, 2022). By logging the entire lifecycle of each product—from raw ingredient sourcing to pharmacy distribution—companies can swiftly identify compromised batches and halt their circulation. This level of transparency not only safeguards patients but also helps firms meet stringent regulatory demands in various jurisdictions.
Similarly, the food sector benefits from blockchain’s immutable record-keeping. IBM’s Food Trust initiative exemplifies how participants throughout the food supply chain—producers, distributors, and retailers—can share validated data securely (PwC, 2024). In the event of a contamination scare, stakeholders can trace the affected products within minutes, isolating the source and minimizing public health risks. This capability is particularly impactful in emerging markets, where food safety issues and adulteration are persistent concerns. A blockchain-enabled system provides local suppliers a straightforward method to prove compliance with international standards, opening up new export opportunities (KPMG, 2022).
Cross-industry collaborations around blockchain are on the rise, forming consortiums where diverse entities exchange data without relinquishing ownership or compromising security. This approach has been especially beneficial in electronics and mineral sourcing, where multiple companies verify the authenticity and ethical origin of components or raw materials (Deloitte, 2023). By default, a decentralized ledger prevents unilateral data manipulation, ensuring that no single participant can distort records for personal gain. In emerging economies, such consortiums enable small and medium enterprises (SMEs) to align with global supply chain demands, leveraging blockchain-based solutions without bearing the entire infrastructure cost.
Smart Contracts: These self-executing protocols operate on blockchain to automate contractual obligations. In supply chains, they can trigger actions like payment releases upon confirming delivery or automatically reorder inventory when stock hits predefined levels (Korpela, Hallikas, and Dahlberg, 2020). This automation mitigates human error, enhances trust, and accelerates transaction times by removing intermediaries.
Decentralized Identity Management: Traditional supply chains grapple with verifying identities across multiple geographies and platforms. Decentralized identity frameworks store cryptographic credentials on the blockchain, enabling secure and user-controlled verification without exposing sensitive personal information (EY, 2025). This solution is especially crucial in emerging markets where formal identification systems may be incomplete or inconsistently enforced.
Blockchain-Enabled Data Sharing and AI Integration: When combined with AI, blockchain can facilitate collaborative analytics while preserving data confidentiality. Automotive manufacturers might share encrypted production data to anticipate part shortages or schedule maintenance proactively, leveraging AI models to convert these pooled datasets into actionable insights (PwC, 2024). Because the underlying ledger ensures data integrity, trust barriers between competing entities decrease, fostering wider cooperation and more accurate forecasts.
Blockchain and cryptographic applications in supply chains are evolving to address scalability, interoperability, and regulatory acceptance (Gupta, Gupta, and Kumari, 2022). Although early adopters face challenges related to network latency, transaction costs, and patchwork legal frameworks, incremental technological advancements—like layer-2 scaling solutions or improved consensus protocols—promise to bridge these gaps. In parallel, greater standardization and government endorsement will likely accelerate adoption, particularly as organizations witness tangible benefits like reduced fraud, faster recalls, and enhanced consumer trust.
By leveraging blockchain’s transparent and tamper-resistant environment, supply chains can fortify operational resilience, protect sensitive information, and cultivate stronger stakeholder relationships (KPMG, 2022). In both developed and emerging economies, the ongoing maturation of cryptographic solutions will enable a shift from siloed, paper-based record-keeping to collaborative, digital ecosystems capable of meeting modern demands for speed, accountability, and security. Consequently, blockchain stands poised to remain a cornerstone technology in building the next generation of intelligent, data-secure supply chain networks (EY, 2025).
8.3. Managing Supply Chain Disruptions
Predictive risk analysis has become a cornerstone of modern supply chain management, harnessing AI and data analytics to anticipate and mitigate potential disruptions. In an environment where global interdependencies expose companies to a range of threats—from natural disasters and geopolitical upheavals to supplier insolvencies and logistics bottlenecks—this predictive capability is increasingly critical (Sodhi and Tang, 2020). By examining vast datasets and employing machine learning models, predictive risk analysis can reveal patterns that help firms respond proactively to emerging challenges, thereby reducing costs, safeguarding revenues, and enhancing overall supply chain resilience (KPMG, 2023).
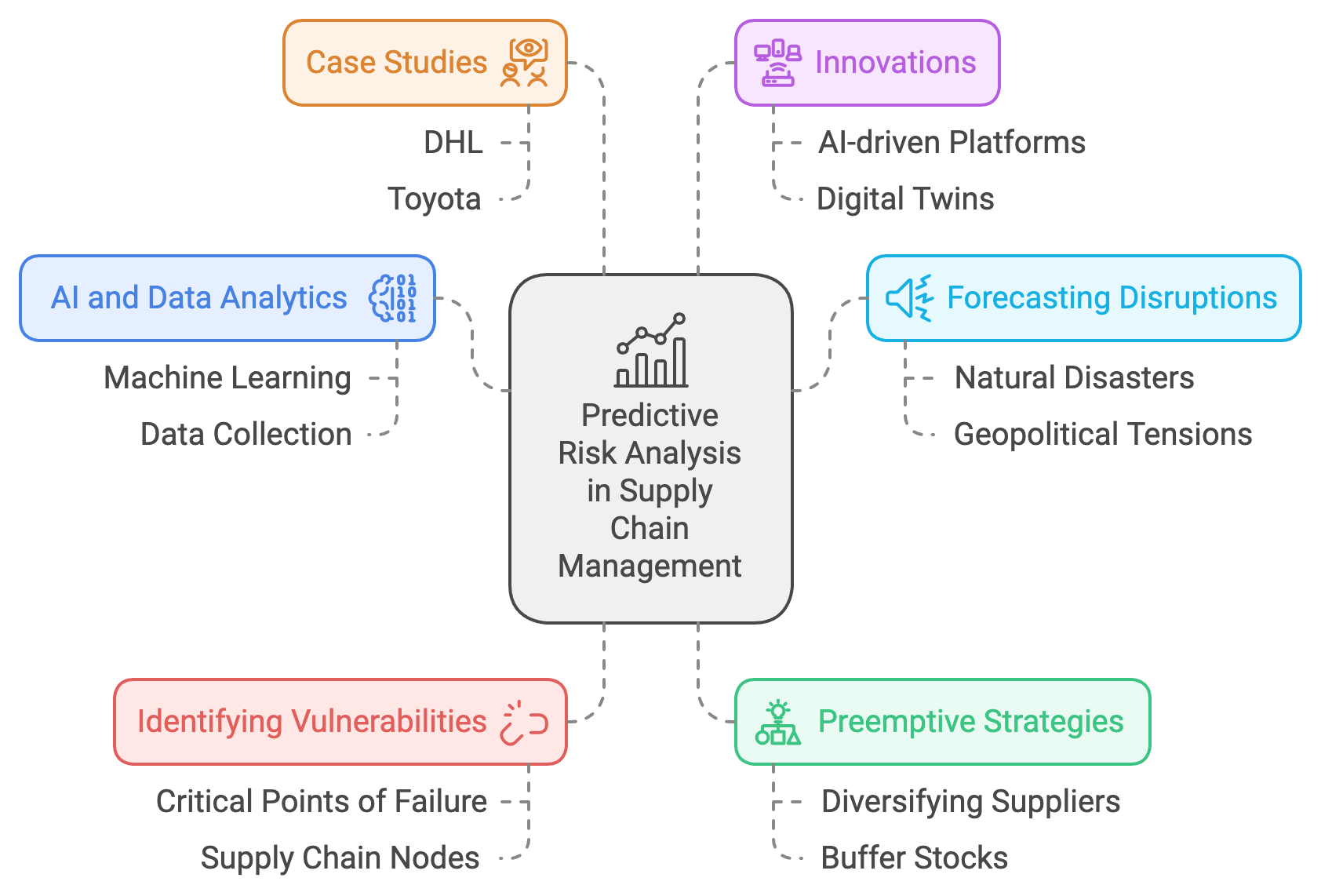
Figure 3: Scopes and Complexities of Predictive Risk Analysis.
Unlike traditional reactive approaches, predictive risk analysis seeks to identify vulnerabilities before they materialize (Yadav, Jain, and Sharma, 2022). Data sources may include weather forecasts, political reports, historical disruptions, and real-time logistics data, providing a comprehensive view of potential supply chain threats. By pinpointing critical failure points—such as a single source for a vital component or reliance on a high-risk transportation corridor—firms can devise contingency plans and diversify their risk exposure (PwC, 2024). This level of preparedness is especially beneficial in emerging markets, where infrastructure instability or sudden regulatory changes can exacerbate disruptions (EY, 2025).
Academically, predictive risk analysis intersects fields such as data science, systems engineering, and risk management. Studies affirm that businesses using advanced analytics for risk mitigation respond more effectively to disruptions, whether anticipated (like seasonal demand spikes) or unexpected (like natural disasters or sudden policy shifts) (Mani, Delgado, and Hazen, 2021). In addition, these proactive strategies foster trust among stakeholders and partners, as timely alerts and transparent communication help maintain service continuity and customer satisfaction (Sodhi and Tang, 2020).
DHL’s Risk Management Platform: Global logistics provider DHL employs an AI-driven platform to track geopolitical developments, market trends, and weather patterns, issuing early warnings for potential interruptions (KPMG, 2023). This enables DHL to reroute shipments or scale back operations in high-risk zones, while also communicating effectively with clients about delays or alternative options. By leveraging real-time insights, DHL can redistribute resources, secure alternate transportation modes, and minimize disruption-related costs.
Toyota’s COVID-19 Response: During the COVID-19 pandemic, Toyota utilized predictive analytics to monitor evolving demand patterns and identify potential supplier shortfalls (Deloitte, 2021). Its system analyzed indicators like regional pandemic outbreaks, port congestion, and commodity price fluctuations to anticipate bottlenecks in component supply. This foresight allowed Toyota to pivot production schedules, diversify suppliers, and adjust inventories in a timely manner, preserving both customer satisfaction and operational efficiency (Mani, Delgado, and Hazen, 2021).
Procter & Gamble’s Demand Fluctuation Management: Consumer goods giant Procter & Gamble adopted AI-driven models to predict and manage surges in demand for household essentials, particularly during pandemic-induced lockdowns. Predictive risk tools enabled the company to tweak production volumes, mobilize additional warehousing capacity, and secure transport routes before shortages or congestion occurred (PwC, 2024). This proactive posture helped P&G navigate disrupted logistics networks and volatile consumer behavior, maintaining availability of key products.
AI-Driven Risk Analysis Platforms leverage data from diverse sources—including satellite imagery and social media sentiment—to use machine learning for highly accurate risk forecasting (Sodhi and Tang, 2020). As these models continuously ingest new data, they refine their predictive power, enabling companies to identify subtle correlations and emerging threat vectors earlier.
Digital Twins create virtual models of physical supply chains, allowing firms to assess the effects of possible disruptions—such as port closures or raw material shortages—before they materialize (Mani, Delgado, and Hazen, 2021). Through what-if analyses, businesses can optimize contingency strategies, resource allocation, and financial planning. These virtual models also enable small and medium enterprises (SMEs) in emerging markets to explore multiple operational configurations without interrupting real-world activities (EY, 2025).
Real-Time Visibility and Analytics integrate IoT sensors with cloud-based analytics platforms to deliver continuous insight into shipments, inventory status, and production lines (Yadav, Jain, and Sharma, 2022). When coupled with predictive algorithms, this live data pinpoints early warning signals—such as delayed cargo or irregular production cycles—and triggers automated alerts or interventions that help companies respond swiftly to potential issues.Predictive risk analysis holds particular promise for emerging economies, where infrastructure volatility and regulatory uncertainties can quickly escalate supply chain challenges (KPMG, 2023). By adopting AI-driven risk assessment tools, local firms can enhance visibility across fragmented logistics networks and respond proactively to sudden obstacles—be it a flood-prone region or volatile currency shifts. This capability levels the playing field, empowering companies in developing regions to meet global quality and reliability standards (EY, 2025). Moreover, the data-driven insights gleaned from predictive models can guide policymakers in refining infrastructure investments and regulatory policies, ultimately fostering a more conducive environment for trade and industrial growth (Sodhi and Tang, 2020).
Managing supply chain disruptions in today’s volatile global climate is becoming a mission-critical undertaking for businesses across industries. Through predictive risk analysis, companies can pinpoint potential issues earlier, devise contingency strategies, and allocate resources more efficiently (Deloitte, 2021). The synergy of AI platforms, digital twins, and real-time analytics creates a robust framework for risk mitigation, enabling organizations to adapt swiftly and maintain operational continuity. As evidenced by industry leaders like DHL, Toyota, and Procter & Gamble, the benefits extend to improved service levels, cost savings, and heightened resilience. For emerging economies in particular, embracing predictive risk analysis can significantly bolster their global competitiveness by providing clarity, agility, and confidence in the face of uncertain market dynamics (PwC, 2024). By systematically integrating these advanced tools and processes, modern supply chains are better equipped to thrive amid ever-evolving threats and opportunities.
8.4. Business Continuity Planning
Business Continuity Planning (BCP) has become an indispensable strategy for organizations aiming to maintain resilience amid the unpredictability of global supply chains (Sodhi and Tang, 2020). At its foundation, BCP lays out a proactive framework designed to uphold critical operations—even in the face of disruptions such as natural disasters, geopolitics, cyber incidents, and pandemics (Deloitte, 2023). When applied to supply chain management, BCP focuses not only on preserving the movement of goods and services but also on safeguarding relationships with suppliers, logistics providers, and customers. Through risk assessment, resource allocation, and disaster recovery strategies, companies fortify their ability to adapt quickly, thereby minimizing both financial losses and reputational damage (KPMG, 2023).
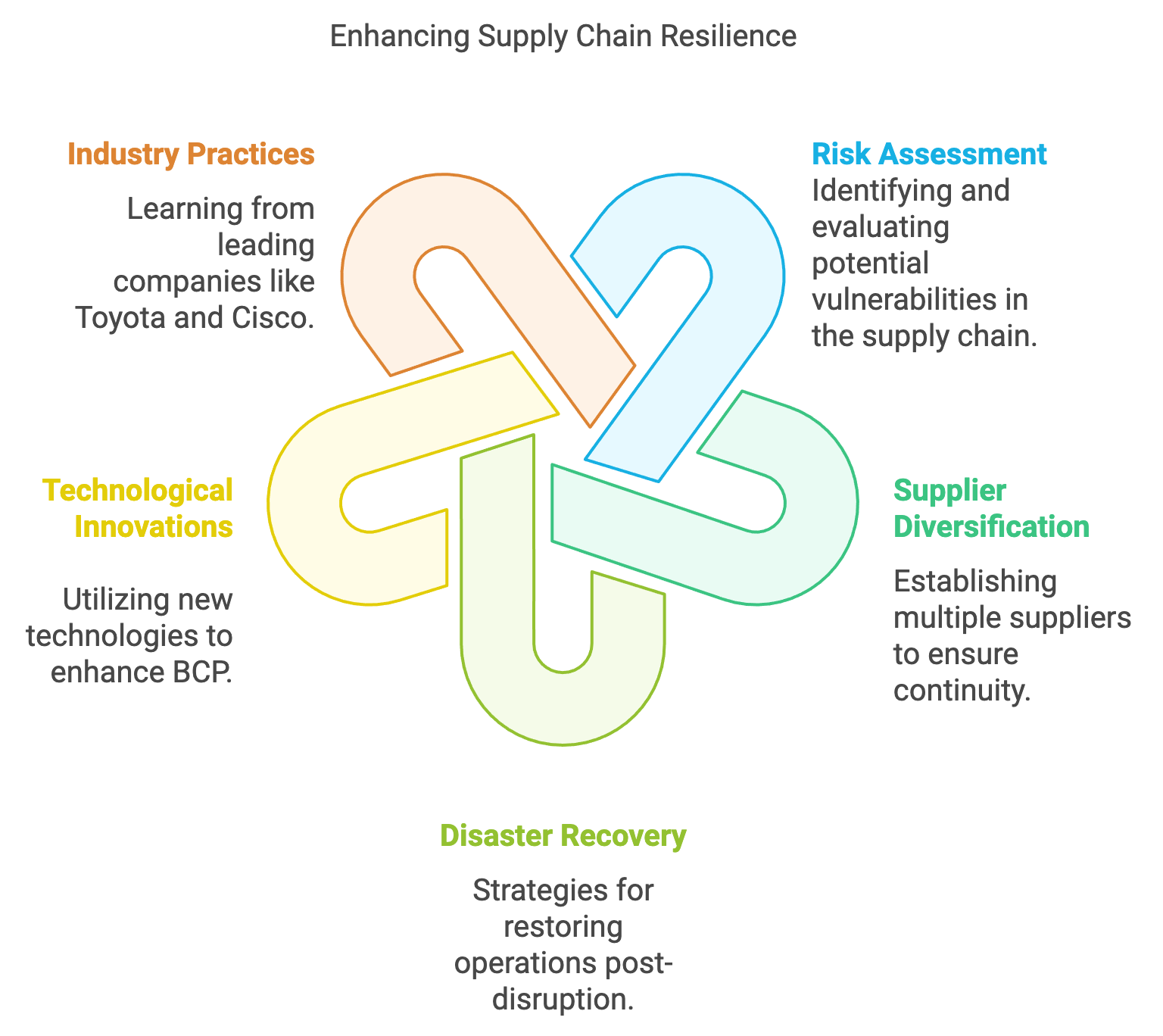
Figure 4: Strategy to enhance supply chain resilience.
At its heart, effective BCP involves identifying potential weak links or “critical points of failure” across the supply chain network. This could be a sole-source supplier, a single-mode transportation route, or a region prone to natural disasters (PwC, 2024). Once vulnerabilities are recognized, business continuity plans call for strategies such as diversifying suppliers, establishing buffer stocks, or developing alternative logistics pathways (Sodhi and Tang, 2020). Effective disaster recovery further details the procedures and tools required to restore operations promptly, emphasizing defined roles, streamlined communication channels, and flexible workflows.
Research underscores the importance of robust BCP for organizational resilience (Mani, Delgado, and Hazen, 2021). In emerging markets, where infrastructure may be less developed and political volatility more frequent, these plans can be even more pivotal. Having clear continuity protocols and diversified operational models helps firms manage unanticipated market shifts, bolstering both local and global partnerships (EY, 2025).
Toyota’s Post-2011 Earthquake Strategy: Following the 2011 Great East Japan Earthquake, Toyota reinforced its BCP framework to mitigate future disruptions. The company diversified its supplier base and heightened inventory reserves of critical components, ensuring that production could continue even if primary suppliers were compromised. This enhanced resilience proved valuable during subsequent global crises, including the COVID-19 pandemic (KPMG, 2023). By systematically integrating redundancies into its supply network, Toyota effectively minimized downtime and maintained steady output.
Cisco’s Supplier and Logistics Diversification: Global technology leader Cisco exemplifies how proactive BCP can drive agility in rapidly changing markets (Deloitte, 2023). The firm maintains relationships with multiple suppliers in various regions, enabling it to recalibrate sourcing in response to political tensions, regulatory shifts, or transportation bottlenecks. This multi-tiered approach also leverages advanced analytics tools to continuously monitor emerging threats, helping Cisco pivot quickly and reduce the risk of catastrophic supply chain breakdowns (PwC, 2024).
These cases highlight the value of structured BCP, emphasizing both redundancy and close supplier collaboration. Such strategies pave the way for rapid adaptation and continued service delivery—even during acute disruptions (Mani, Delgado, and Hazen, 2021).
Recent developments in cloud computing have revolutionized how organizations coordinate continuity planning (Deloitte, 2023). By centralizing risk assessment, communication protocols, and real-time data analytics, these platforms create a unified dashboard for monitoring disruptions. Managers can quickly evaluate the status of suppliers, inventory levels, and transportation routes, accelerating decision-making and reducing operational downtime.
Artificial intelligence is increasingly used to synthesize large datasets—covering meteorological trends, financial indicators, and geopolitical signals—and generate predictive insights (PwC, 2024). When disruptions such as severe weather or strikes become imminent, AI-driven models provide actionable recommendations, guiding managers on whether to reroute shipments, expand inventory buffers, or switch suppliers. This data-driven adaptability is particularly beneficial in volatile regions, where timely response can significantly curtail losses.
Digital twin technology offers a simulated environment in which companies can test the resilience of their continuity strategies (Mani, Delgado, and Hazen, 2021). A digital twin replicates supply chain assets—warehouses, transport routes, and production facilities—to explore hypothetical scenarios like port closures, labor shortages, or currency fluctuations. This risk-free experimentation allows businesses to refine contingency measures, optimize resource allocation, and establish new best practices (EY, 2025). For companies operating in emerging economies with limited logistical infrastructure, digital twins can yield insights without jeopardizing real-world operations.
For firms in regions with fragile infrastructure or heightened political risks, BCP can be a transformative asset. By systematizing risk assessments and establishing backup arrangements, these companies reduce their susceptibility to market shocks, effectively leveling the playing field with global competitors (Sodhi and Tang, 2020). BCP also fosters investor confidence, as multinational partners and suppliers tend to prefer collaborations with enterprises that demonstrate robust continuity protocols (KPMG, 2023). Over time, strong BCP practices in emerging economies can also stimulate better local infrastructure development and policy support, further reinforcing supply chain stability (EY, 2025).
Business continuity planning is more than a defensive measure; it is a strategic imperative for modern supply chains. By conducting thorough risk evaluations, diversifying operational nodes, and employing innovations such as cloud-based coordination platforms, AI-driven modeling, and digital twins, organizations can ensure rapid recovery from disruptions and sustain competitive advantage (Deloitte, 2023). Whether in developed or emerging markets, a well-designed BCP framework underpins resilience, fosters stakeholder trust, and lays the groundwork for long-term growth (PwC, 2024). As demonstrated by Toyota and Cisco, the ability to adapt swiftly to shocks is not only a hallmark of operational excellence but also a key driver of strategic success.
8.5. Conclusion and Further Learning
In conclusion, as supply chains become more digitized and interconnected, the risks they face—cybersecurity threats, disruptions, and global uncertainties—grow more complex. By integrating advanced technologies such as AI-driven predictive risk analysis, blockchain for data security, and robust business continuity plans, companies can build more resilient and secure supply chains. The proactive management of cybersecurity risks and the implementation of innovative strategies will be essential to maintaining operational continuity and safeguarding the future of global supply chains.
Engaging with the following prompts will deepen your understanding of how cybersecurity, predictive risk analysis, and business continuity planning are reshaping the landscape of modern supply chains. By exploring these topics, you will uncover valuable insights into how businesses can protect their supply chains from cyber threats, anticipate disruptions, and build resilient, adaptable systems for the future.
How can companies proactively identify and mitigate cybersecurity risks in digital supply chains, considering vulnerabilities in IoT devices, cloud infrastructure, and third-party suppliers, and what role does AI play in enabling real-time threat detection, anomaly detection, and automated response strategies to minimize breaches and operational disruptions?
What are the critical vulnerabilities within supply chains that cybercriminals frequently target, such as unsecured endpoints, third-party vendor risks, and data integrity issues, and how can businesses implement multi-layered cybersecurity defenses, including encryption, threat intelligence sharing, and incident response planning, to protect against ransomware attacks and data breaches?
How do zero-trust security frameworks function within the context of supply chains, particularly in verifying identities, limiting access, and securing communications across interconnected digital networks, and why are these frameworks essential for safeguarding highly automated and globalized supply chain operations?
How does blockchain technology ensure the integrity, transparency, and immutability of data across global supply chains, and what are its key applications in sectors such as pharmaceuticals and food safety, particularly in preventing counterfeiting, ensuring product authenticity, and enhancing traceability in real-time logistics management?
What are the primary benefits of applying cryptographic techniques, such as hashing, encryption, and digital signatures, to secure data exchanges within supply chains, and how do these methods protect sensitive information, verify the authenticity of transactions, and prevent unauthorized access or data tampering in cross-border operations?
How can smart contracts, integrated with blockchain technology, enhance security within supply chain processes by automating regulatory compliance, enforcing contract terms, and verifying the legitimacy of transactions, and what industries are leading the way in adopting these innovations to improve operational transparency and reduce fraud risks?
What are the best practices for implementing predictive risk analysis in supply chains, and how can AI-driven platforms leverage big data, machine learning algorithms, and real-time analytics to forecast and prevent disruptions caused by supply chain vulnerabilities, external risks, and operational inefficiencies?
How can companies utilize digital twin technology to create virtual simulations of their supply chains, enabling them to model potential disruptions, assess risk scenarios, and test risk mitigation strategies in real-time, and what are the most effective ways to integrate these simulations into continuous supply chain monitoring and decision-making processes?
What are the critical success factors for integrating predictive risk analysis into existing supply chain operations, including the use of advanced data analytics, real-time risk monitoring tools, and cross-functional collaboration, and how can businesses optimize their risk mitigation strategies to improve supply chain resilience and flexibility?
How can predictive analytics help companies manage the impact of external factors such as geopolitical risks, natural disasters, and market volatility on their supply chains, and what technologies can be used to identify early warning signals, model potential outcomes, and develop proactive response plans to ensure business continuity?
What are the key components of a comprehensive business continuity plan (BCP) for supply chains, and how can these plans be regularly updated and adapted to address emerging global uncertainties, including regulatory changes, pandemics, and technological disruptions that could impact global logistics and supplier networks?
How can cloud-based platforms improve business continuity planning by enabling real-time risk monitoring, data centralization, and collaboration across complex supply chain networks, and what specific functionalities, such as disaster recovery and automated response capabilities, should be integrated into these platforms to ensure rapid response to crises?
What role do AI-powered decision support systems play in helping companies adapt business continuity plans in response to real-time data, enabling dynamic scenario analysis, supply chain simulations, and predictive insights that allow leaders to make faster, more informed decisions during disruptions or crises?
How can companies measure the effectiveness of their business continuity plans in maintaining operational resilience during major supply chain disruptions, and what key performance indicators (KPIs), such as recovery time objectives (RTO), service-level agreements (SLAs), and risk mitigation outcomes, should be used to assess their success?
How does blockchain technology enhance the security of data-sharing processes in cross-industry supply chain collaborations, and how does it build trust between partners by providing a decentralized, tamper-proof ledger for tracking and verifying transactions, product origins, and compliance with regulatory standards?
What are the biggest challenges in securing IoT devices and sensors that are increasingly used in supply chains for real-time tracking, monitoring, and automation, and how can businesses overcome these vulnerabilities by adopting best practices in device authentication, network encryption, and end-to-end security protocols?
How can businesses integrate cybersecurity best practices, such as multi-factor authentication, continuous monitoring, and advanced encryption methods, into their overall risk management frameworks to protect both digital assets and physical operations from cyberattacks and other threats to supply chain integrity?
How can companies ensure that their business continuity plans remain flexible and responsive to unexpected, high-impact global events such as pandemics, trade wars, and economic crises, and what strategies can be implemented to ensure that these plans include adaptive supply chain routing, supplier diversification, and crisis communication protocols?
What are the key benefits of diversifying suppliers, logistics routes, and manufacturing locations as part of a robust business continuity strategy, and how can companies balance the costs and risks associated with maintaining multiple supply chain contingencies to improve resilience and reduce dependency on single points of failure?
How can predictive risk analysis and AI-driven platforms enable businesses to make faster, data-driven decisions to minimize the impact of potential supply chain disruptions, and what role do these technologies play in continuously optimizing supply chain processes for greater agility, resilience, and operational continuity?
These prompts will challenge you to think critically about the role of cutting-edge technologies and proactive strategies in ensuring supply chain security and continuity. Embrace these questions to gain the expertise needed to safeguard the supply chains of tomorrow and lead in an ever-evolving, interconnected world.
Comments